7 Best Practices for Incident Response (IR) & Recovery
As a business owner, you don’t know when your system will be the next target of a cyberattack. However, having a solid incident response, or IR plan, can significantly reduce the impact, financial damage, and duration of the cyber threat.
A well-devised incident recovery plan can make sure that your business successfully transitions from the cyberattack disruptions to normal operations without any data loss, minimal downtime, and a proven strategy to bounce back from similar threats in the future. However, only 55% of businesses have a fully documented IR plan, and nearly half of the companies are unprepared when a breach happens.
This blog discusses incident response, its 4 phases, and the 7 best strategies for the NIST framework. It also takes you through the details of incident recovery, tools and technologies, and the common IR challenges.
What is Incident Response?
An incident response is a set of procedures, activities, and practices that are designed to address and resolve cyber attack incidents, such as a data breach, disruption in services, and unauthorized access.
According to research, the organizations that do not have a formal structured IR plan pay around 58% more per cyber breach incident as compared to the businesses that have a proper incident IR plan.
Without a defined plan, the teams often have no idea how to manage and respond to cyber threat/attack incidents and react haphazardly. However, the incident response and recovery plan provide a proper strategy to react to cyber threats and guide every step of detection, action, and remediation.
Whether the cybersecurity incident is a ransomware, a phishing attack, or a zero-day vulnerability, an efficiently designed incident response can detect, contain, and eliminate the incident. The ultimate goal of incident response is to hold on to the evidence, allow transparency, and prevent similar recurrences.
The 4 Phases of Incident Response (NIST Framework)
The NIST incident response framework is adopted largely by most businesses that want to deal with cyber threats with a well-documented plan.
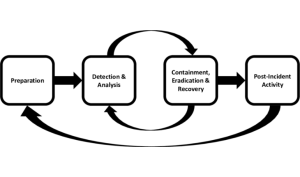
Here is the description of the 4 phases of the IR process:
- Preparation: The first phase discusses establishing the foundation. This includes the necessary documents, policies, response teams, tools, and all other resources that effectively contribute to responding to a cyber incident.
- Detection and analysis: At this stage, the security teams validate the incident response. They collect data that shares information about the scope, severity, nature, and potential operational, financial, and reputation damage it may cause.
- Containment, Eradication, and Recovery: The containment process involves isolating the affected system in order to prevent its impact from spreading further. After the impact is contained, the eradication process begins, which includes techniques like vulnerability patching, malware removal, and securing the entry and backdoor points.
- Post-incident activity: The final stage of the NIST framework focuses on restoring the services. It includes:
- Documenting the details of the incident.
- Performing a root cause analysis of how the system was exploited and how the response could have performed better.
- Improving the incident response plans and policies to enhance the detection and response capabilities.
7 Best Practices for Effective Incident Response
Apart from creating financial and operational damages, a cyber incident can raise serious reputational risks. According to a survey, 70% of customers prefer not to purchase from a brand that faced a security incident recently.
Thus, creating a solid IR plan is essential, but executing it under pressure correctly to minimize the chances of any type of damage is paramount. Here are the top 7 best practices that you can implement for developing an effective incident response:
1. Design a cross-functional incident response team
Dealing with cybersecurity incidents is not limited to the IT team. Different teams have to face the impact and the consequences, thus build a team with executive leadership from tech, HR, legal, and cybersecurity experts. If hiring an on-site team is expensive, then you can outsource these capabilities to a trusted incident-response provider, like Agency 1987, to secure your infrastructure.
2. Perform regular monitoring and detection
A cyber incident can occur anytime; the moment you think you are safe, a cyber threat can exploit your system. Therefore, continuously monitor threats using automated monitoring tools with behavioral analytics to detect incidents, anomalies, and risks. Once the defect is identified, timestamp it with its nature, severity, scope, and potential impact.
3. Ensure your incident response plan is active and ready-to-use
Your IR plan should not be a stored file that needs to be searched through the folders; it should be a living document that is accessible anytime. It should define the escalation triggers, privilege and authorization levels, digital evidence handling, external communication procedures, and regulatory reporting requirements.
4. Make use of realistic simulations
Implement scenario-based drills to help refine response procedures, red-team(attackers)-blue team(defenders) drill, and validation of detection times.
5. Create offline backups
Threats like ransomware often attack systems that lack clean, accessible backups. Make sure to maintain offline, encrypted backups that are stored away from your production networks.
6. Document every aspect of the incident
From the reporting of the first incident to the latest encounter, record everything. Precise documentation regarding every incident can strengthen legal defense, forensic claims, compliance reporting, and improve the IR plan.
7. Improve the IR plan post-attack
Restoring the systems post-cyber incident doesn’t mean the task is done.
- You should perform post-incident reviews to identify key learning points, weaknesses, and understand how the security processes responded to the attack.
- Modify your policies, security controls, and communication plans.
- Educate and train teams and security professionals with new guidelines and actionable techniques for incident response.
- Finally, make strategic improvements in the IR plan to prepare for upcoming threats.
Incident Recovery: What to do After the Attack?
You are done with the incident response, and now you want your systems to switch back to their original operational state. While the method seems simple, it involves multiple incident recovery workflows, such as:
- Before restoration, security teams validate that the threat has been completely removed from the features, processes, endpoints, or accounts.
- Refreshing the credentials, password resets, and credential access reevaluation is performed to remove unimportant accesses.
- Vulnerability patching and correcting configurations in the existing systems are done to prevent similar cyber incidents.
- Teams set clear communication regarding the incident response and recovery across clients, partners, and stakeholders. This eliminates misinformation and reduces panic.
- Complete details of the incident, IR strategies implemented, policy changes, and training details are documented, reported, and maintained for future use.
Tools & Technologies That Support IR
Different types of tools and technologies are used to deal with different aspects of the incident response process:
- Endpoint security/monitoring tools: Endpoint detection and response (EDR) and Extended detection and response (XDR) are used to protect endpoints such as mobiles, desktops, and laptops from potential threats.
- Cybersecurity incident response service providers: Managed detection and response (MDR) IR service bundles, EDR, XDR, and other security tools to identify and analyze threats and provide remediation. Security Information and Event (SIEM) gathers and normalizes log data from different sources, like firewalls and antivirus systems, and provides a real-time analysis of the security events.
- Vulnerability scanners: These scanners are designed to detect potential vulnerabilities across systems, networks, and multiple applications.
- Threat intelligence platforms: These platforms collect data about emerging threats from different sources such as social media, dark web forums, and hacker groups, and provide this information to organizations.
- IDPS: The intrusion detection and prevention systems regularly track network traffic and activities performed on the system. It uses techniques like signature or behavior-based detection and anomaly detection to discover any upcoming threats.
Common Incident Response Challenges
Despite a successful IR plan, many businesses may face challenges related to incident response:
- Insufficient cyber incident information might result in teams struggling to understand the scope, nature, and full-scale impact on the system. Thus, continuously training the teams about the latest cyber incidents, threats, and attacks is essential, and make sure to document every detail of the incidents encountered.
- Too many notifications create alert fatigue within the teams. The security professionals might spend too much time with low-priority risks and unknowingly overlook major cyber incidents. Therefore, make sure to prioritize the threats and cyber incidents.
- Limited tools for monitoring, detecting, and mitigating threats can make organizations miss critical threats.
- Ensure to integrate IR with the latest tools and technologies.
- Perform a rigorous post-incident response workflow to ensure every component of the system is free from the cyber incident impact.
Conclusion
An efficient incident response and recovery plan is no longer optional; it is an essential workflow to achieve cybersecurity resilience. By creating a thoroughly designed IR plan using the best practices for incident response and implementing complete incident recovery strategies, you can ensure that your systems survive, recover, and come back stronger from any cyber incident.
Looking for services to design an IR plan for your business? Agency 1987 can be your perfect partner to develop incident response and recovery workflows according to your business needs. Contact us today!
Frequently Asked Questions
1. Does every business need an IR plan?
A. Every business can be a target for a cyber threat or an incident. So, having an IR plan is a must for every business.
2. How long will it take to recover from a cyber incident after the incident response and recovery have been implemented?
A. It depends on the type and severity of the cyber incident. Some may take hours, while other serious threats may take months for the system to recover.
3. How frequently should I update the IR plan?
A. You should update the IR plan at least twice a year after addressing minor cyber incidents. But after a faceoff with a major cyber threat, you should update the IR plan without any delay.
