10 Signs Your Business Needs a Penetration Test (VAPT)
Your business might be power-packed with strong methods to encounter cyberattacks, but dealing with a cybercrime after the attack has taken place is difficult, as by that time, the cyberattack might have already impacted your business processes.
Adopting techniques that help you uncover your business vulnerabilities beforehand can bring advantages in terms of uninterrupted operations, maintained customer trust, and prevention from financial losses before a threat turns into a crisis.
One such technique is vulnerability assessment and penetration testing (VAPT). It is a testing method that helps businesses identify hidden risks and vulnerabilities that an attacker might exploit to break into the system.
In this blog, we will discuss what penetration testing is, its types, benefits, and 10 signs that your business needs penetration testing.
What Is a Penetration Test?
Penetration testing is a type of security testing for businesses that is also commonly known as ethical hacking. It involves security professionals and ethical hackers who perform simulated cyberattacks on the system. The goal of the penetration testing (or a pen test) is to validate how the system behaves when a cyberattack takes place or when a hacker exploits the system’s vulnerabilities.
Through pen-testing, organizations can verify the strengths of the system across different networks, teams, APIs, cloud, and security mechanisms deployed throughout the system.
Three different approaches can be adopted when performing penetration testing:
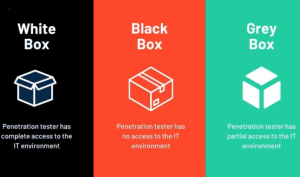
- Black box pen-testing approach
In this approach, the ethical hacker or the security professional takes the role of the uninformed black hat attacker and performs the simulation like an attacker with little to no information about the system. This approach identifies the existing system vulnerabilities and is the longest type of pen-tests that may take upto several weeks to deliver results.
- White box pen-testing approach
The pen tester has complete knowledge of the system, access to the source code, and the system environment. The simulations performed using this approach reveal in-depth details about the code quality, misconfigurations, and the absence of any defensive measures.
- Gray box pen-testing approach
The ethical hacker or the pen tester has somewhat information about the system, configurations, and a basic idea about how the system will respond to the simulation. Simulations performed can exploit user privileges, access to code, and provide a clearer assessment of the security network of the system.
10 Clear Signs Your Business Needs a Penetration Test
When to apply a penetration test is a question that confuses most businesses, resulting in delays in testing, leading to increased vulnerabilities. Therefore, if you are facing any of the following scenarios, it’s time to run a penetration test:
- You recently upgraded to a new system or launched a new application: Every new launch or system upgrade comes with its own set of vulnerabilities. Performing a pen test can ensure your upgrade or launch does not expose data or information.
- Compliance adherence: This is especially important for businesses in industries like finance, healthcare, and payments. Several regulations standards, like PCI-DSS, require businesses to perform internal and external testing annually; similarly, HIPAA demands regular risk analysis and assessments, etc.
- Recently experienced a security breach: Performing a pen-test becomes critical if you have recently experienced any data leakage or a security breach. It helps identify more hidden vulnerabilities.
- Dealing with sensitive data: If you are dealing with any sensitive information, then performing a pen-test can help discover gaps related to weak encryption, unauthorized access, etc.
- You are expanding into new markets: When you expand your services in new regions, offices, or remote work settings, you open up new endpoints and integrations for attackers to exploit. Thus, performing a VAPT test becomes crucial to identify gaps.
- You are completely dependent on automated security scans: Although automated checks are efficient, they may fail in finding chained attacks or discovering logic vulnerabilities.
- You have not performed a pen-test for quite some time: Since cyber threats and attackers constantly change their attacking strategies, running a pen-test can help ensure your system remains active.
- You are undergoing a merger or acquisition: When you merge or acquire new systems, you unknowingly expose your system to new vulnerabilities. A pen-test can help validate that your security standards are intact.
- There has been an update in your industry’s security standards: If there is any change in the state data privacy laws, regulation standards, or industry guidelines, you must run a penetration test to check that there are no security gaps and your system remains compliant.
- Your customers or partners demand proof of your security demonstration: In case you need to provide proof of your robust security testing and demonstrations, performing a pen test can build customer trust and bring a competitive advantage.
What Does a Vulnerability Assessment and Penetration Testing Service Include?
VAPT is a combined cybersecurity approach that includes vulnerability analysis and penetration testing. Both approaches are critical for businesses as they proactively encounter cyber risks, test defense mechanisms, and strengthen the system’s capability to prevent and respond to cyberattacks.
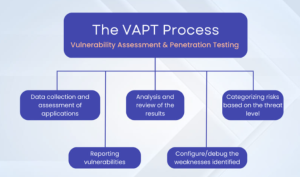
- The vulnerability assessment is an automated process that identifies vulnerabilities such as misconfigurations, insufficient access controls, or any unsafe API.
- The penetration testing involves performing a real-world simulation of a cyber attack and checking how the security controls respond to the attack.
VAPT services include different types of penetration testing techniques, such as:
- Network penetration testing: Performs pen-testing for the networked components present, such as firewalls, routers, switches, etc. The internal tests verify the risks on the internal network, and external testing checks for any vulnerabilities by simulating attacks outside the network.
- Mobile penetration testing: Evaluates vulnerabilities on mobile applications such as weak permissions, insecure storage, etc.
- Web application penetration testing: It performs testing to check vulnerabilities on the web applications, such as session hijacking, SQL injection, etc.
- Social engineering penetration testing: It evaluates the security controls for social engineering tactics. It involves testing methods like phishing, pretexting, and granting unauthorized access.
- Hardware penetration testing: Performs testing on hardware components such as IoT devices, networked appliances, and other integrated devices.
Benefits of Running a Penetration Test
85% of the businesses that adopted strong security measures, including VAPT, reported enhanced business performance. Here are some of the important VAPT benefits:
- Proactive vulnerability identification: As discussed earlier, VAPT allows businesses to detect gaps and loopholes before a cyberattacker exploits them.
- Reinforces brand reputation: If you perform regular VAPT for your business, it shows your customers and stakeholders that you are actually committed to safeguarding your systems.
- Measures compliance with security controls: VAPT can help businesses ensure that the processes adhere to global standards and regulations like HIPAA, GDPR, PCI-DSS, etc.
- Uncovers multi-layer vulnerabilities: The VAPT methods can identify risks across different layers, including web, mobile applications, wireless systems, APIs, and across your internal business teams.
- Real-life simulation: Penetration tests are performed using real-world scenarios. This helps in understanding how an attack would take place, how the system responds, and how your defense systems may fail.
How Often Should a Business Run Penetration Tests?
Penetration testing is not a one-time security testing approach; it should be performed at regular intervals to address ongoing and evolving vulnerabilities.
- An annual penetration testing should be performed to meet compliance standards. It makes sure that your organization complies with the latest regulatory requirements.
- A penetration test should be conducted after every major system update. This helps in discovering that new features or functionalities do not create security gaps.
- After cloud migrations, the pen-test should be performed regularly, immediately after the migration, and every two or three months to check that there are no potential risks developed that can compromise your internal or external components.
Conclusion
Protecting your business software with firewalls and modern antivirus, antimalware solutions is not enough. You need efficient security testing techniques like VAPT that offer a strategic approach to discover system weaknesses before cybercriminals weaponize them.
Adopting pen-testing techniques at the right time will make sure that your system remains compliant, secure, robust, reliable, and trustworthy for customers and partners.
Agency 1987 is the leading provider of cybersecurity services, including VAPT services like testing for mobile security, web applications, wireless testing, social engineering, etc. Contact us today to learn how you can validate your systems using our advanced cybersecurity services.
Frequently Asked Questions
1.How long will it take to complete a penetration test?
A. It depends on the testing approach, techniques used, scope, and the environment of the test. For example, the pen-tests performed using the black box approach may take several weeks to complete.
2. Is VAPT automated?
A. VAPT combines both automated vulnerability assessment and manual pen-testing techniques.
3. Does performing VAPT guarantee that the system cannot be hacked?
A. No security testing can provide the guarantee of a system that cannot be hacked. However, by performing VAPT, you can minimize the chances of cyber attacks by identifying the risks and the security gaps before a cyber criminal exploits them.
